
In today’s complex network infrastructure comprised of diverse resources, devices, and users, port scans represent a significant amount of network traffic. Crackers and hackers alike use port scanners to discover port vulnerabilities that can become attack vectors to malicious outcomes.
In this post, we discuss the fundamentals of port scanning, and why you need to deploy an effective port scanner software on your network right now.
What is a port scanner?
A port scanner helps you detect a potential security breach by identifying the hosts connected to your network and the services running on them, such as the file transfer protocol (FTP) and hypertext transfer protocol (HTTP).
An advanced port scanner, like ManageEngine OpUtils, provides you with an in-depth view into your network ports. This includes details like, connected IP, DNS, and MAC, along with name and details about the interface associated with a particular port. A network port scanner also enables you to identify and close all the open ports in your networks.
Port scanning ensures your network hosts are configured to run only approved network services, and prevents ports from allowing any unauthorized traffic.
Quick fact
With ports serving as the communication gateways for your network, misconfigurations of open ports can lead to denial of service (DoS) attacks.
How does a port scanner work?
A port scanner inspects your entire IP address block to identify active hosts within the specified IP address range, using network protocols like Transmission Control Protocol (TCP) and Internet Control Message Protocol (ICMP).
Once a network port scanner has discovered the active hosts in the given address range, it scans the host for TCP and User Datagram Protocol (UDP) ports. These ports are the pathways of communication between the host and other network devices. This tool then scans ports to identify the services running on them, and pinpoint open ports.
Determining the status of scanned ports
A port scanner determines the status of the ports using different network scanning protocols, by sending a network packet to each port within the specified address range, one at a time. Based on the response received from the ports, it determines their status as listening or non-listening ports.
Types of network scans used
Network ports are scanned using multiple network scanning protocols to ensure pulling-out accurate data on the status and services running on the ports. The most commonly used port scans are:
Ping scans
These ICMP scans sweep the entire IP address block, or a single target IP, to check and see if the target is up. After sending an echo request, if the target sends an ICMP reply, this scan determines the target is up.
TCP scan
This is a commonly used port scan by port scanning tools that carries out a complete handshake process with the target to determine its status. The port scanner initially sends the target a synchronization (SYN) request. On receiving the SYN flag, the target sends the scanner a synchronization-acknowledgement (SYN-ACK). The port scanner then sends a ACK packet denoting that it has received the target’s SYN-ACK response. Based on the response received, the port scanner determines the status of the network ports.
UDP scan
A UDP scan attempts to find open UDP ports in a network. It is a connection-less protocol that works by sending a network packet to the target. This network packet usually carries no payload, but it can be set to carry a random payload for each port. Based on the ICMP response received from each target, the port scanner determines the status of the target.
Why do you need to use a port scanner?
In order to secure your network environment, and ensure stable network functioning, it is crucial to track all the entities accessing your network resources.
Ports serve as the communication endpoints in a network, and any service running on them can easily gain access to sensitive data in the target machine. It is imperative to monitor and track all services running on your ports and associated network devices.
Quick fact
Crackers and hackers find TCP ports are an easier targets because they utilize a connection-oriented protocol that can provide useful feedback to the attacker. UDP ports use a connection-less protocol that does not necessarily provide relevant information for an attacker.
The risks of not using an port scanning tool:
Open port vulnerabilities: Some ports might remain continually open, presenting a potential network vulnerability. An intruder can access an open port to wreak havoc in the normal flow of network operations.
Data leakage: Network ports should be closely monitored by an effective advance network port scanning tool to avoid any data leakage. This also helps secure communications between the computing entities in the network.
Utilizing an effective port scanner tool like OpUtils helps you eliminate risk vectors, and is imperative for securing your network against unauthorized access, and malicious monitor services running on your ports.
Quick fact
Remote desktop protocol (RDP) ports allow communication with remote systems, and are vital for enabling the workforce of many businesses to operate out of their homes. However, these ports are often insecurely exposed to the internet, making them an easy target for attackers.
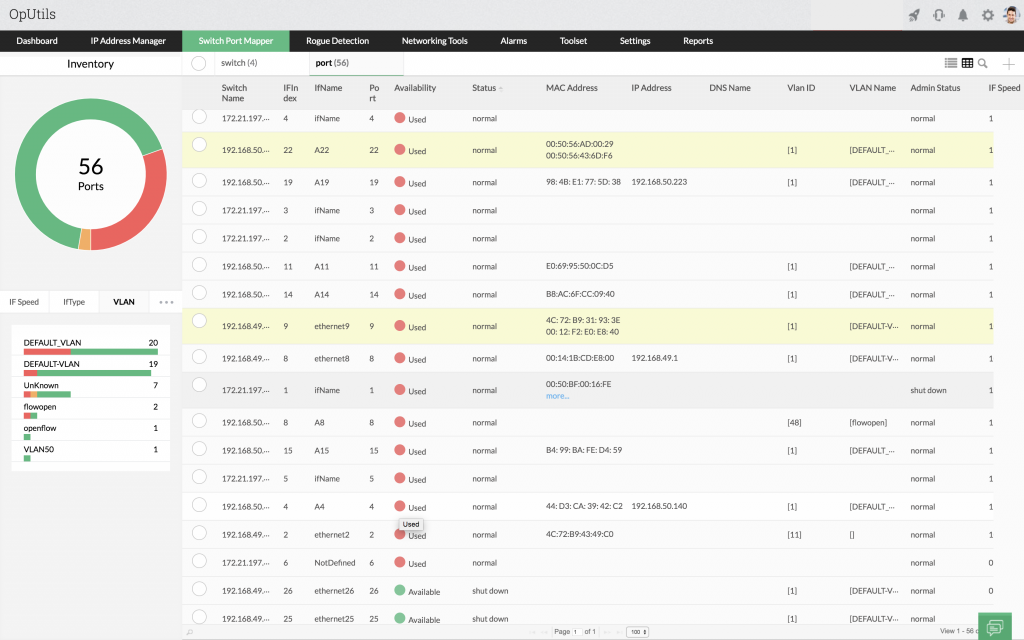
Advanced port scanning with OpUtils
Oputils’ advanced port scanner tool helps you perform network reconnaissance on your ports and switches. On a large network, monitoring and managing open ports can be extremely time-consuming. OpUtil’s advanced port scanning capabilities determine the status of ports in your network by attempting to connect to all the port within the specified IP range. It provides insights into:
- The network host or hosts that are up and running in the target IP address range
- The services that are currently running
- The users of the services
- The state of the network ports in the target machine
Obtaining these insights with a advance port scanner helps you conduct network port and service identification so you can distinguish hosts, and flag potentially vulnerable services.
Ports and services
Machines connected to a network can run many services that use TCP or UDP ports to communicate with each other. These network ports are usually numbered from 0 to 65535, with different ports running different services, and each having a service name such as Telnet. These services run over network protocols, such as TCP, UDP, Datagram Congestion Control Protocol (DCCP), and Stream Control Transmission Protocol (SCTP)
Ports can be categorized into three large ranges:
- Well-known ports (0-1023)
- Registered ports (1024-49151)
- Dynamic and/or private ports (49152-65535)
Well-known ports or standard ports have been assigned to commonly used internet services. OpUtils’ port scanner tool allows you to scan these well-known ports, along with the other network ports, by specifying the port range to be scanned.
Some of the common ports and services scanned by OpUtils’ port scanner are:
21 – File Transfer Protocol (FTP) – Transfer files between computers over the internet
22 – Telnet – Remote login service, unencrypted text messages
23 – Telnet – Remote login service, unencrypted text messages
25 – Simple Mail Transfer Protocol (SMTP) – Email routing
53 – Domain Name System (DNS) – IP address naming database
80 – Hypertext Transfer Protocol (HTTP) – Internet connectivity
110 – Post Office Protocol 3 (POP3) – Email clients
143 – Internet Message Access Protocol (IMAP) – Digital Mail
161 – Simple Network Management Protocol (SNMP) – To manage and monitor network devices
3389 – Remote Desktop Protocol (RDP) – Secure network communications protocol
Quick fact
Commonly hacked and comparatively more vulnerable ports in networking are FTP (21/TCP), SMTP (25/TCP), HTTPS (443/TCP), and HTTP (80/TCP).
Features of OpUtils advanced port scanner
Oputils’ port scanning software obtains the list of services currently running on the ports scanned within the given IP range. This can be compared to the known list of services which enables you to pinpoint and block unauthorized services running on the network ports.
With advanced port scanning abilities, OpUtils enables you to:
- View real-time mapping of the switch ports in the network, and drill down to the physical location of ports.
- Pull a comprehensive summary of network ports that provide full visibility into their status.
- Create automated port scan schedules that are triggered periodically to obtain an accurate summary of network ports utilization and performance metrics.
- Generate instantaneous, threshold-based alerts for switch-port specific events.
- Conduct network audits easily with advanced port scanning widgets that provide crucial data at a glance
- Enable or disable ports to secure networks from unauthorized access and traffic flow.
- Provide role-based access management to allow multiple users with access to network port scanning and monitoring.
That’s not all! Visit our port scanner feature page to learn more about everything you can do with OpUtils advanced port scanning.
 New to ManageEngine OpUtils? Schedule a live demo with a product expert who will walk you through all the features of OpUtils, or download a 30-day free trial and learn hands-on how OpUtils can enhance your IP address and switch port management strategy.
New to ManageEngine OpUtils? Schedule a live demo with a product expert who will walk you through all the features of OpUtils, or download a 30-day free trial and learn hands-on how OpUtils can enhance your IP address and switch port management strategy.

